🚨 Apple's Passwords app was vulnerable to phishing attacks in iOS versions prior to 18.2. Its functionality to change a password from within the app used to open an account's website via insecure HTTP by default. This allowed an attacker with privileged network access to easily… pic.twitter.com/VrqFWSk4z1
— Mysk 🇨🇦🇩🇪 (@mysk_co) March 18, 2025
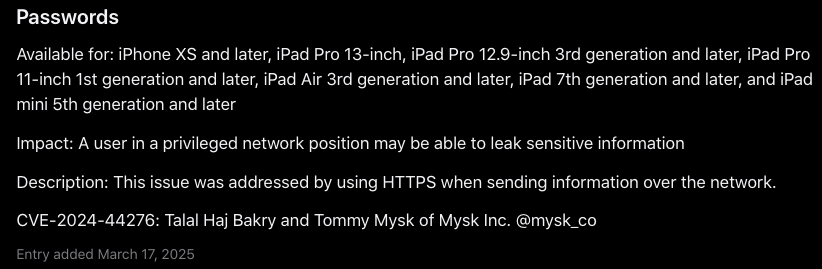
Apple’s iOS 18 update, which was released back in September last year, brought along a lot of new features and changes. One of them was a new, built-in Passwords app. The app, as the name suggests, makes it easy for users to manage their credentials across apps and websites. While it was definitely a welcome addition, it has now come to light that the app had a security vulnerability which persisted until December last year when it was fixed in iOS 18.2.
Popular iOS developers and security researchers who go by the name Mysk revealed this a few hours ago on X.
In layman terms, you can understand it this way. At launch in September, the Passwords app used the HTTP protocol (instead of the more secure HTTPS) to connect to the websites whose credentials you are managing. So, during the 3-months (September-December) period, anyone clicking on a link stored in the app would have created an opportunity for a hacker to redirect the request (to open the legit website) to a phishing website wherein the user could have given away their credentials to the hacker easily.
The following videos shows the proof of how this could have been done:
Thankfully, this is the only use case that could have been exploited through this vulnerability, which means auto-fill of passwords wasn’t impacted in any way. And considering the fact that very few users usually open links through a password management app, and also the fact that the hacker also needed to be on the same network as the user, it’s unlikely that users were targeted at scale. In fact, there are no known reports of anyone being hacked by exploiting this vulnerability.
However, exploited or not, a vulnerability is still a vulnerability. Speaking to 9to5Mac, the security researchers said they were amazed Apple didn’t use HTTPS to begin with.
We were surprised that Apple didn’t enforce HTTPS by default for such a sensitive app. Additionally, Apple should provide an option for security-conscious users to disable downloading icons completely. I don’t feel comfortable with my password manager constantly pinging each website I maintain a password for, even though the calls Passwords sends don’t contain any ID
Apple officially disclosed this vulnerability on March 17.
TechIssuesToday primarily focuses on publishing 'breaking' or 'exclusive' tech news. This means, we are usually the first news website on the whole Internet to highlight the topics we cover daily. So far, our stories have been picked up by many mainstream technology publications like The Verge, Macrumors, Forbes, etc. To know more, head here.