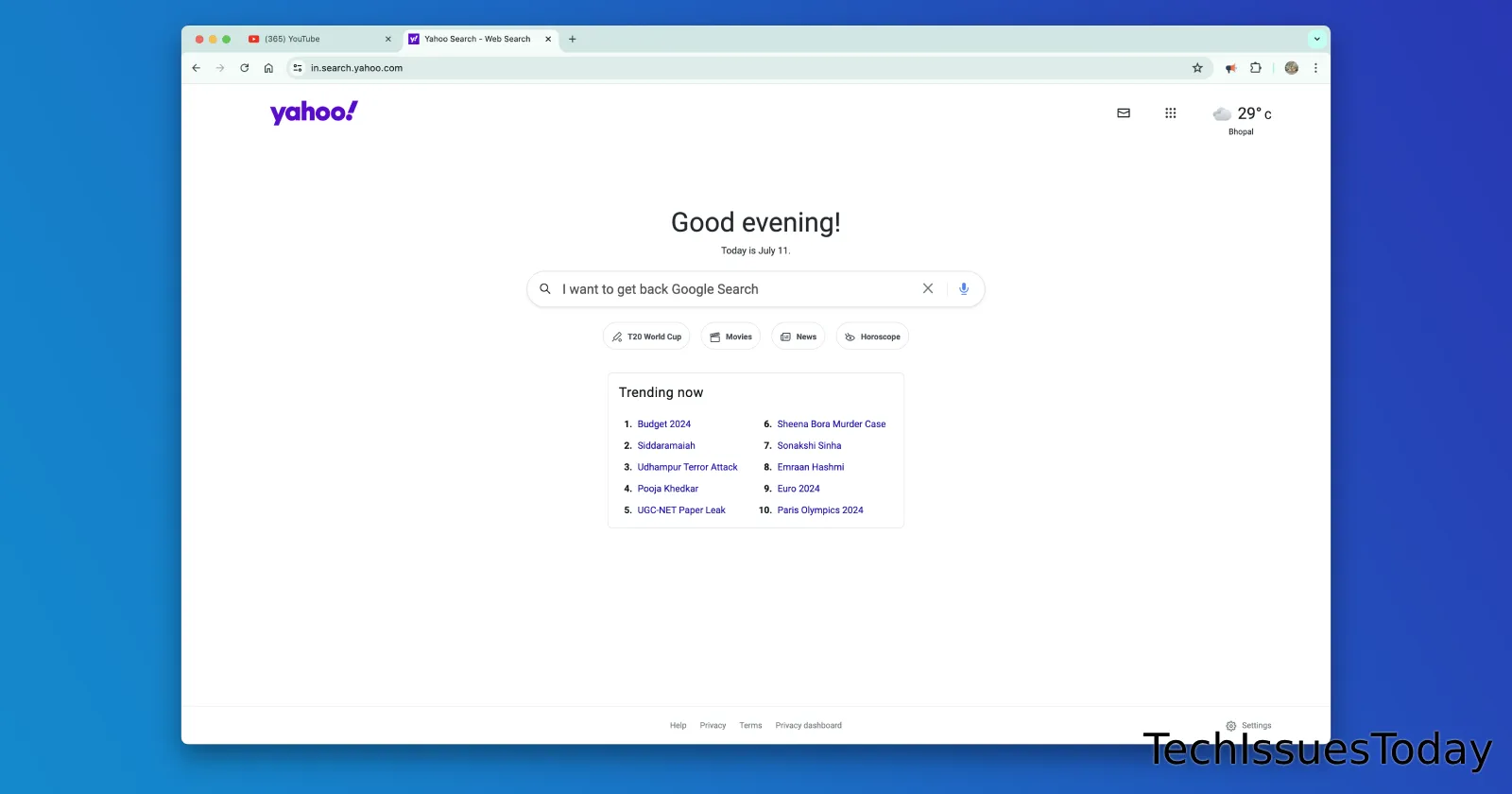
In the vast landscape of internet browsers, Google Chrome stands as a titan, boasting millions of users worldwide. Its seamless integration with Google’s search engine is a key feature that many users appreciate. However, a growing number of Chrome users have reported a perplexing issue: their default search engine suddenly changing to Yahoo without their consent. This unexpected switch can be jarring and frustrating, especially for those who rely on Google’s search capabilities. However, this isn’t a new problem and has been around for years. But don’t fret! I’ve rounded up all the information on why this happens and what you can do to boot Yahoo out of your browser. In case you can’t be bothered digging into “why” it happens and just want to know how to switch back to Google Search, click here to jump to the guide.
Understanding the culprit: Browser hijackers
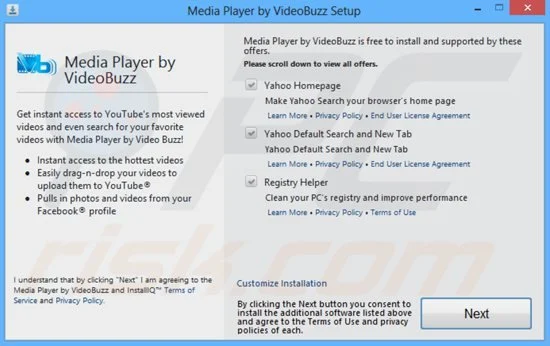
At the heart of this issue lies a type of malware known as a browser hijacker. These malicious programs are designed to infiltrate your web browser and modify its settings without your knowledge or permission. While Yahoo itself is a legitimate search engine with a long history in the tech industry, the method by which it becomes your default search option is usually far from legitimate. However, in some cases, developers provide options during the app’s setup process to ask users whether or not they want to install a Yahoo toolbar or make it the default search engine. In such cases, the decision lies in your hands as the user, so be observant when installing software on your computer. Here’s an example (h/t – PCrisk) of what you might see while setting up an application on your computer:
That said, browser hijackers are a subset of potentially unwanted programs (PUPs) that specifically target web browsers. Their primary goal is to alter your browser settings to redirect your searches, change your homepage, or display unwanted advertisements. In the case of Yahoo Search appearing unexpectedly, a browser hijacker is likely redirecting your searches to Yahoo’s search engine, often for financial gain through affiliate marketing or ad revenue.
How browser hijackers infiltrate your system
Understanding how these unwanted programs make their way onto your computer is crucial for prevention. Browser hijackers typically enter your system through several deceptive means:
- Bundled software: One of the most common methods is through software bundling. When you download free software from the internet, especially from less reputable sources, it may come packaged with additional programs. These extras, including browser hijackers, are often hidden in the fine print of installation agreements or tucked away in “custom” installation options.
- Malicious email attachments: Opening an infected attachment from an email can introduce a browser hijacker to your system. These emails often masquerade as important messages from banks, social media platforms, or other trusted sources.
- Compromised websites: Visiting an infected website might trigger a drive-by download of a browser hijacker. This can happen without you even realizing it, especially if your browser or operating system has unpatched vulnerabilities.
- Fake browser extensions: Some seemingly innocent browser add-ons or extensions may contain hijacking code. These can be found even in official extension stores, although they’re usually removed quickly once detected.
- Freeware and shareware: Some free software and shareware programs include browser hijackers as part of their monetization strategy.
- Peer-to-peer (P2P) networks: Downloading files from P2P networks can be risky, as these files may be bundled with various types of malware, including browser hijackers.
Once installed, a browser hijacker can perform a variety of unwanted actions:
- Change your default search engine (in this case, to Yahoo).
- Modify your browser’s homepage.
- Alter new tab page settings.
- Inject unwanted ads into your browsing experience.
- Track your browsing habits and collect personal information.
- Redirect you to specific websites.
The risks associated with browser hijackers
While changing your search engine to Yahoo might seem relatively harmless on the surface, it’s important to understand that this is often just the tip of the iceberg. Browser hijackers pose several significant risks:
- Privacy concerns: Many browser hijackers are designed to track your browsing habits and collect personal information. This data can be sold to third parties or used for targeted advertising. In more severe cases, it could lead to identity theft or financial fraud.
- Reduced system performance: Browser hijackers often run in the background, consuming system resources. This can lead to slower browsing speeds, increased load times, and overall decreased computer performance.
- Exposure to malicious content: Some hijackers may redirect you to harmful websites that host malware or engage in phishing attempts. These sites might try to trick you into downloading additional malware or entering sensitive information like login credentials or financial details.
- Gateway for other malware: Once a browser hijacker has established itself on your system, it can potentially open the door for more serious malware infections. It might download and install additional malicious software without your knowledge.
- Disrupted user experience: Beyond the annoyance of an unwanted search engine, hijackers can cause other frustrating issues like persistent pop-up ads, new browser windows opening unexpectedly, or your homepage constantly reverting to an unwanted site.
- Financial risks: Some sophisticated hijackers might attempt to capture financial information or redirect you to fake banking sites.
- Data loss: In extreme cases, particularly aggressive malware associated with browser hijackers could lead to data corruption or loss.
Identifying a browser hijacker
Recognizing the signs of a browser hijacker is crucial for prompt action. Here are some telltale indicators:
- Unexpected change in default search engine (e.g., to Yahoo).
- New toolbars or extensions in your browser that you don’t remember installing.
- Homepage changes without your input.
- Increased number of pop-up ads or redirects.
- Slower than usual browsing speeds.
- Difficulty in modifying browser settings.
- New bookmarks added without your knowledge.
- Unusual browser behavior, like new tabs opening automatically.
How to remove Yahoo Search from Chrome
Now let’s get to the interesting part. If you’ve found that Yahoo Search has taken over your Chrome browser, follow this detailed step-by-step guide to remove it and restore your preferred settings:
Option 1: Reset Chrome’s search engine settings
- Open Google Chrome.
- Click the three dots in the upper right corner to open the menu.
- Select “Settings”.
- In the left sidebar, click on “Search engine”.
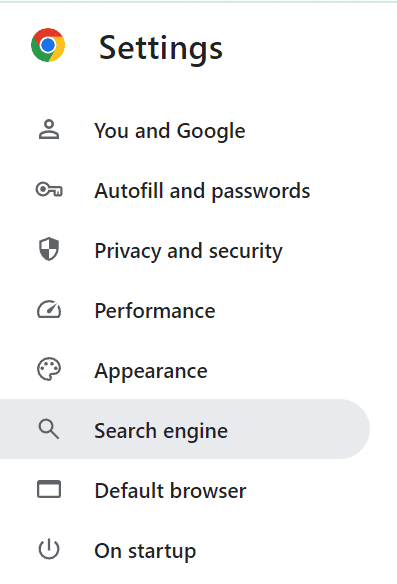
- Under “Search engine used in the address bar,” select your preferred search engine from the dropdown menu.
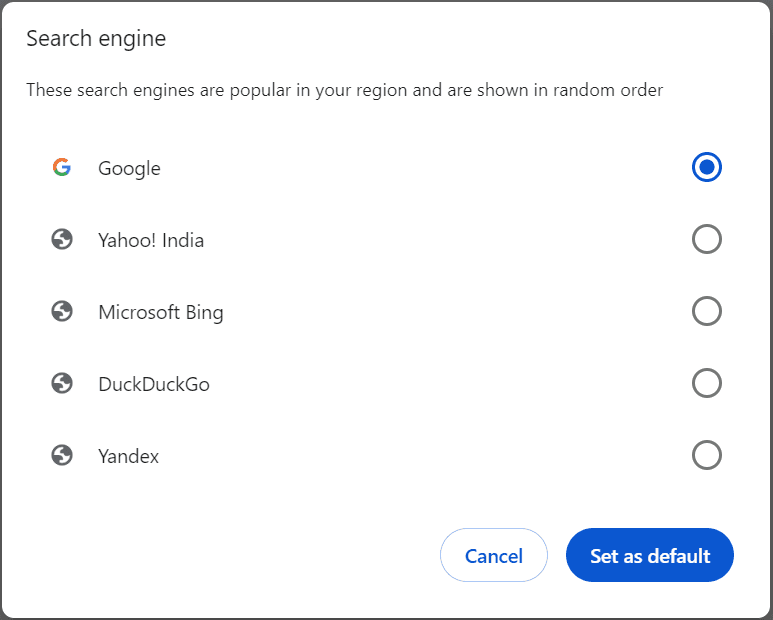
- Once done, you’ll see a pop-up message confirming your action.
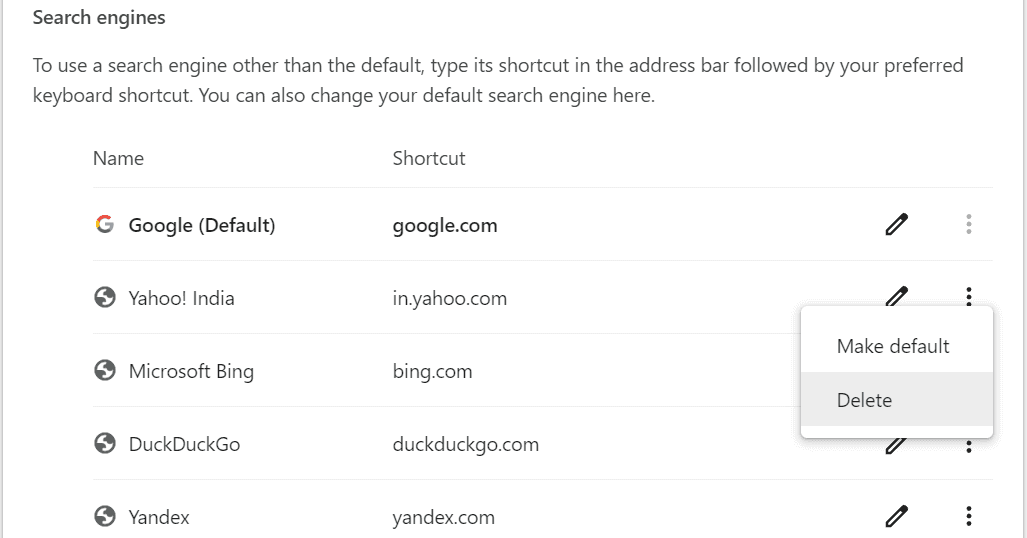
- As a cautionary measure, you can click the “Manage search engines” button and look for Yahoo in the list. If you find it, click the three dots next to it and select “Delete”.
Option 2: Check for and remove suspicious extensions
- Type “chrome://extensions/” in the address bar and press Enter.
- Review all installed extensions carefully.
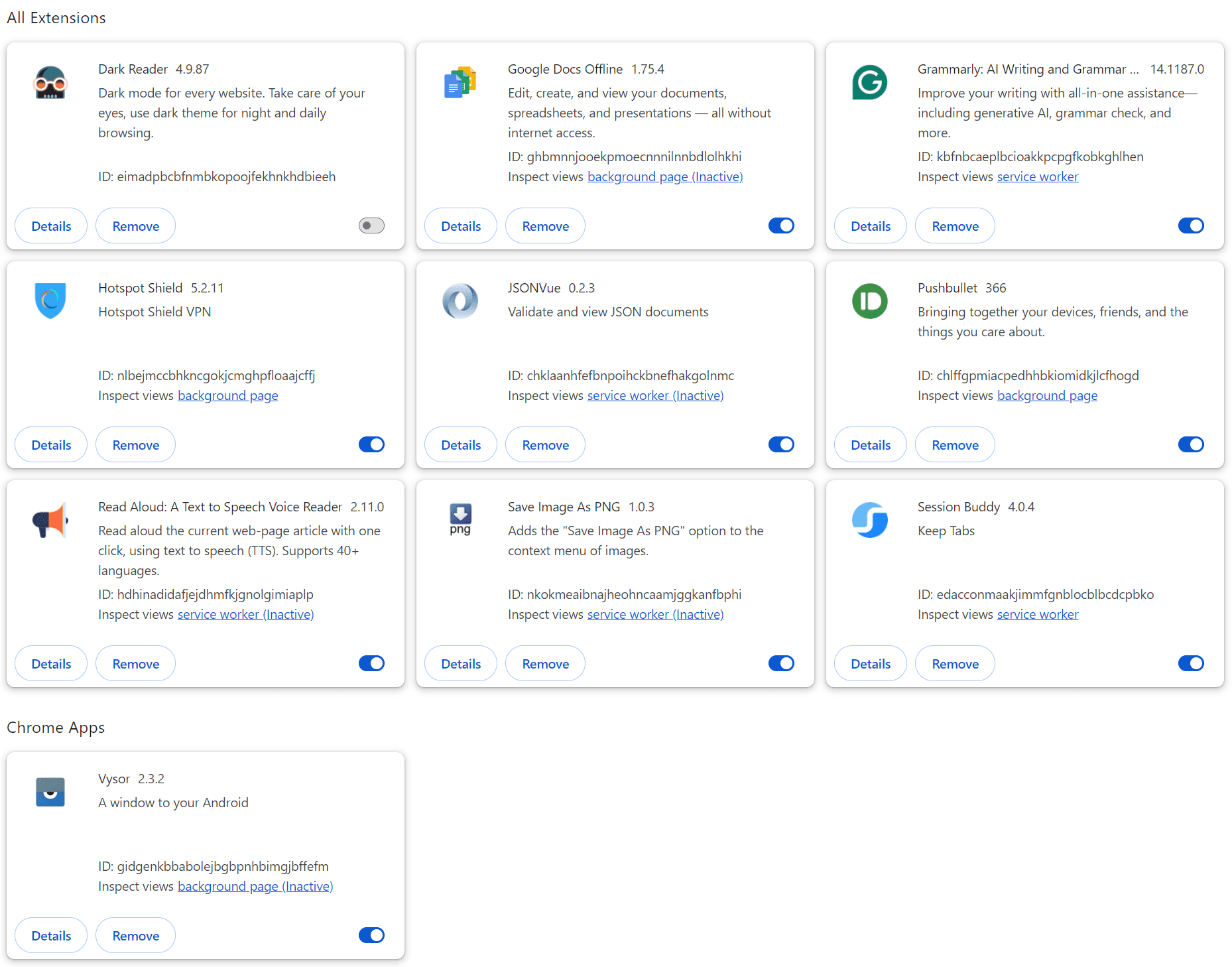
- For any extensions you don’t recognize or trust:
- Click on “Remove” to uninstall it.
- If you’re unsure about an extension, you can temporarily disable it by toggling off the switch, then research it online.
Option 3: Reset Chrome to default settings
- Go back to Settings.
- Select the “Reset settings” option from the sidebar on the left.
- Click on “Restore settings to their original defaults”.
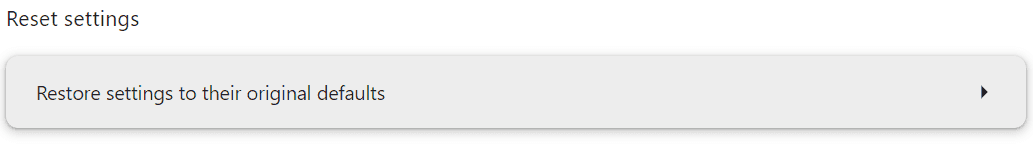
- A confirmation dialog will appear. Click “Reset settings” to confirm.
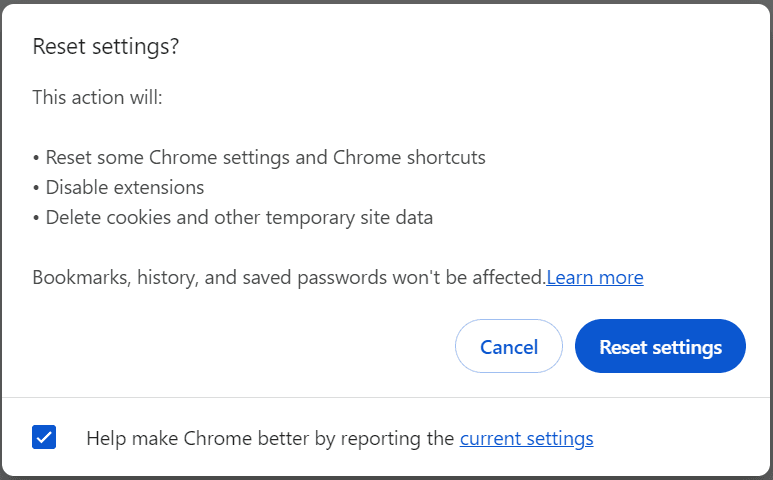
Resetting everything to default means you might have to redo whatever changes you made to Chrome’s settings intentionally.
Option 4: Manually add Google Search as the default search engine
This workaround was suggested by a user and it seems to have worked for some. Here are the exact steps provided by a product expert on Google’s support forums:
- Open the search engines settings (chrome://settings/searchEngines) – (the same page in your screenshot)
- You’ll see an Add button next to the title Site search section title, click on it
- Now you’ll be prompted to add a few info.
– i) Name of the site, simply give “Google”
– ii) Shortcut for the site, enter “google.com”
– iii) URL with search query, type “{google:baseURL}search?q=%s&{google:RLZ}{google:originalQueryForSuggestion}{google:assistedQueryStats}{google:searchFieldtrialParameter}{google:language}{google:prefetchSource}{google:searchClient}{google:sourceId}{google:contextualSearchVersion}ie={inputEncoding}” - Click on Add.
- Now the new Google site search will be added under the Site search section.
- Press on the three dots next to this entry.
- Press on Make default to make it your default search engine.
Option 5: Perform a full system malware scan
- Use a reputable antivirus or anti-malware program.
- Ensure your antivirus software is up to date.
- Perform a full system scan, not just a quick scan.
- If any threats are detected, follow your antivirus software’s recommendations for removal.
Option 6: Check your computer for suspicious programs
For Windows:
- Open the Control Panel.
- Go to “Uninstall a program” or “Programs and Features”.
- Sort the list by “Installed On” date.
- Look for any recently installed programs you don’t recognize.
- Right-click on suspicious programs and select “Uninstall”.
For Mac:
- Open the Finder.
- Go to the Applications folder.
- Review your installed applications, paying special attention to recent additions.
- For any suspicious apps, drag them to the Trash.
- Empty the Trash afterward.
Option 7: Update your browser and operating system
- Ensure Chrome is updated to the latest version:
- Click the three dots > Help > About Google Chrome.
- If an update is available, install it and restart the browser.
- Update your operating system:
- For Windows, check for updates in Settings > Update & Security.
- For Mac, check for updates in System Preferences > Software Update.
Option 8: Consider resetting your network settings
In some cases, browser hijackers can modify your network settings. Resetting these can help:
For Windows:
- Open Command Prompt as Administrator.
- Type the following commands, pressing Enter after each:
- netsh winsock reset
- netsh int ip reset
- ipconfig /release
- ipconfig /renew
- ipconfig /flushdns
- Restart your computer.
For Mac:
- Go to System Preferences > Network.
- Select your network connection.
- Click the “-” button to remove it.
- Click the “+” button to re-add it.
- Restart your computer.
Prevention
Preventing browser hijackers from infiltrating your system in the first place is crucial. Here are some best practices to keep your browser and computer safe:
- Exercise caution when downloading software:
- Always download software from official websites or reputable sources.
- When installing new programs, choose the custom or advanced installation option.
- Carefully read through each step of the installation process.
- Uncheck any boxes for additional software or toolbars you don’t want.
- Keep your software updated:
- Regularly update your operating system.
- Keep your web browser updated to the latest version.
- Enable automatic updates for your antivirus software.
- Use a reliable antivirus program:
- Install a reputable antivirus program or use Windows Defender.
- Ensure real-time protection is enabled.
- Perform regular system scans.
- Be skeptical of email attachments and links:
- Don’t open attachments from unknown sources.
- Be wary of unexpected attachments, even from known contacts.
- Hover over links to preview the URL before clicking.
- Practice safe browsing habits:
- Avoid clicking on pop-up ads or suspicious links.
- Be cautious when downloading files, especially from unfamiliar websites.
- Use a pop-up blocker in your browser.
- Manage browser extensions carefully:
- Only install extensions from official web stores.
- Read reviews and check permissions before installing any extension.
- Regularly review your installed extensions and remove any you no longer need.
- Use strong, unique passwords:
- Use complex passwords for all your accounts.
- Consider using a password manager to generate and store secure passwords.
- Enable two-factor authentication:
- Wherever possible, enable two-factor authentication for your accounts.
Conclusion
While Yahoo Search itself is not malicious, its unexpected appearance as your default search engine often signals a deeper security issue. Browser hijackers are more than just an annoyance; they represent a significant breach in your system’s defenses and can lead to more severe security and privacy issues if left unchecked.
In my experience, based on past instances of running into the same problem, the issue is usually fixable once you uninstall the third-party program you might have installed recently which resulted in it hijacking your browser. Once uninstalled, you can simply perform the steps mentioned in “Option 1” above. I’m confident that this should do the trick for most users.
If you continue to experience issues after following these steps, or if you’re unsure about any part of the process, it may be worth getting in touch with Apple, Microsoft, or Google support (depending on your computer’s OS). They can provide personalized assistance and ensure your system is fully secure.