Recent leaked documents from Cellebrite, an Israeli digital intelligence company, reveal some surprising limitations in their ability to crack open certain smartphone models.
The confidential “iOS Support Matrix” and “Android Support Matrix” from April 2024, obtained and verified by 404 Media, offer a rare peek behind the curtain of phone unlocking technology used by law enforcement agencies worldwide. And let’s just say, some of our devices are putting up quite a fight.
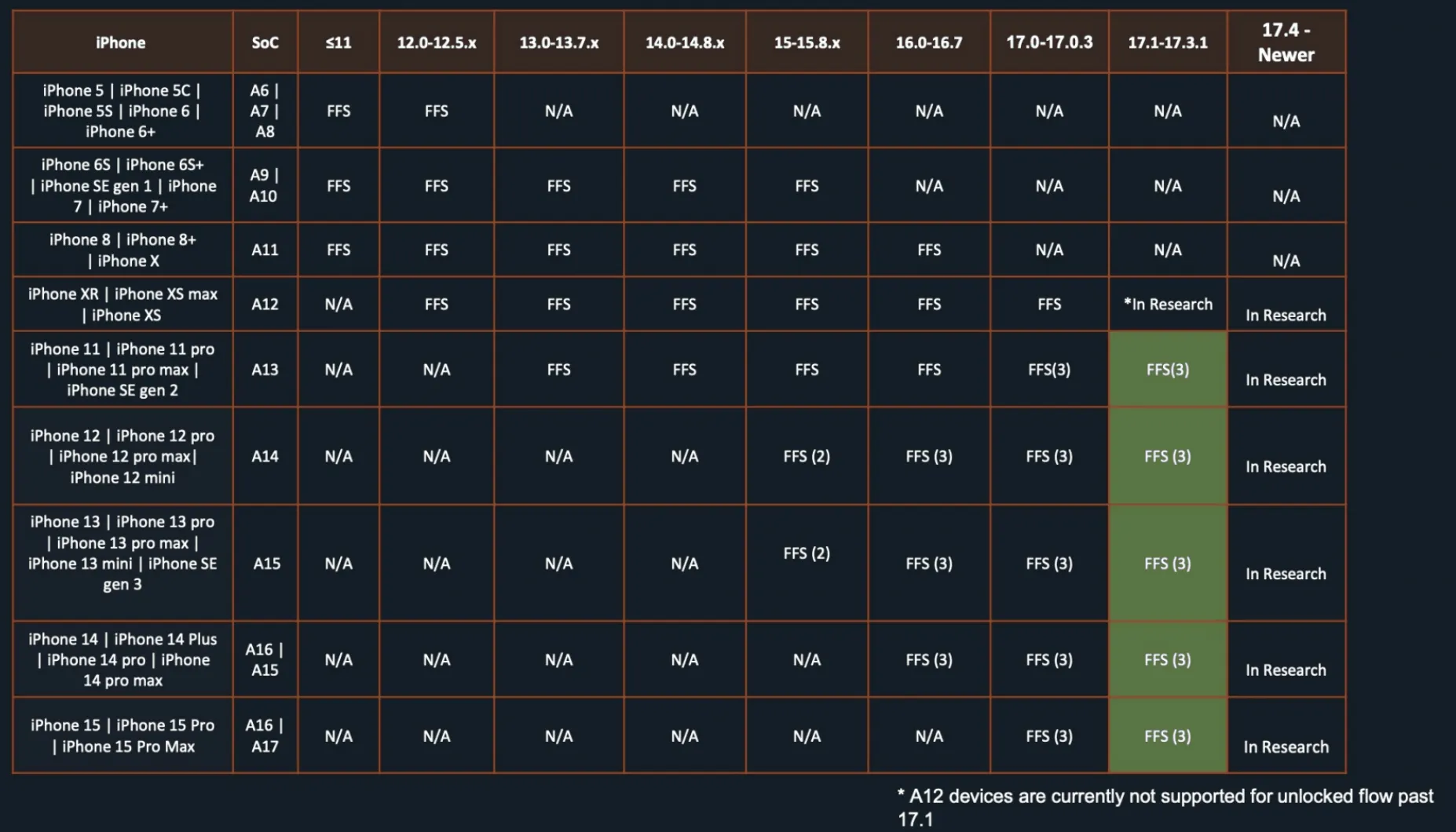
First up, the iPhone. If you’re rocking an iPhone running iOS 17.4 or newer, congratulations – you’ve got Cellebrite scratching their heads. The documents label these devices as “In Research,” which is corporate speak for “we can’t crack ’em yet.” Even for slightly older iOS versions (17.1 to 17.3.1), Cellebrite’s “Supersonic BF” (that’s brute force, not best friend) capability only works on the iPhone XR and 11 series. Anything newer? They’re still working on it.
This limitation is significant, considering Apple reported that 77% of all iPhones and 87% of iPhones introduced in the last four years were running iOS 17 as of June 2024. This leaves a large portion of devices potentially inaccessible to Cellebrite’s current tools.
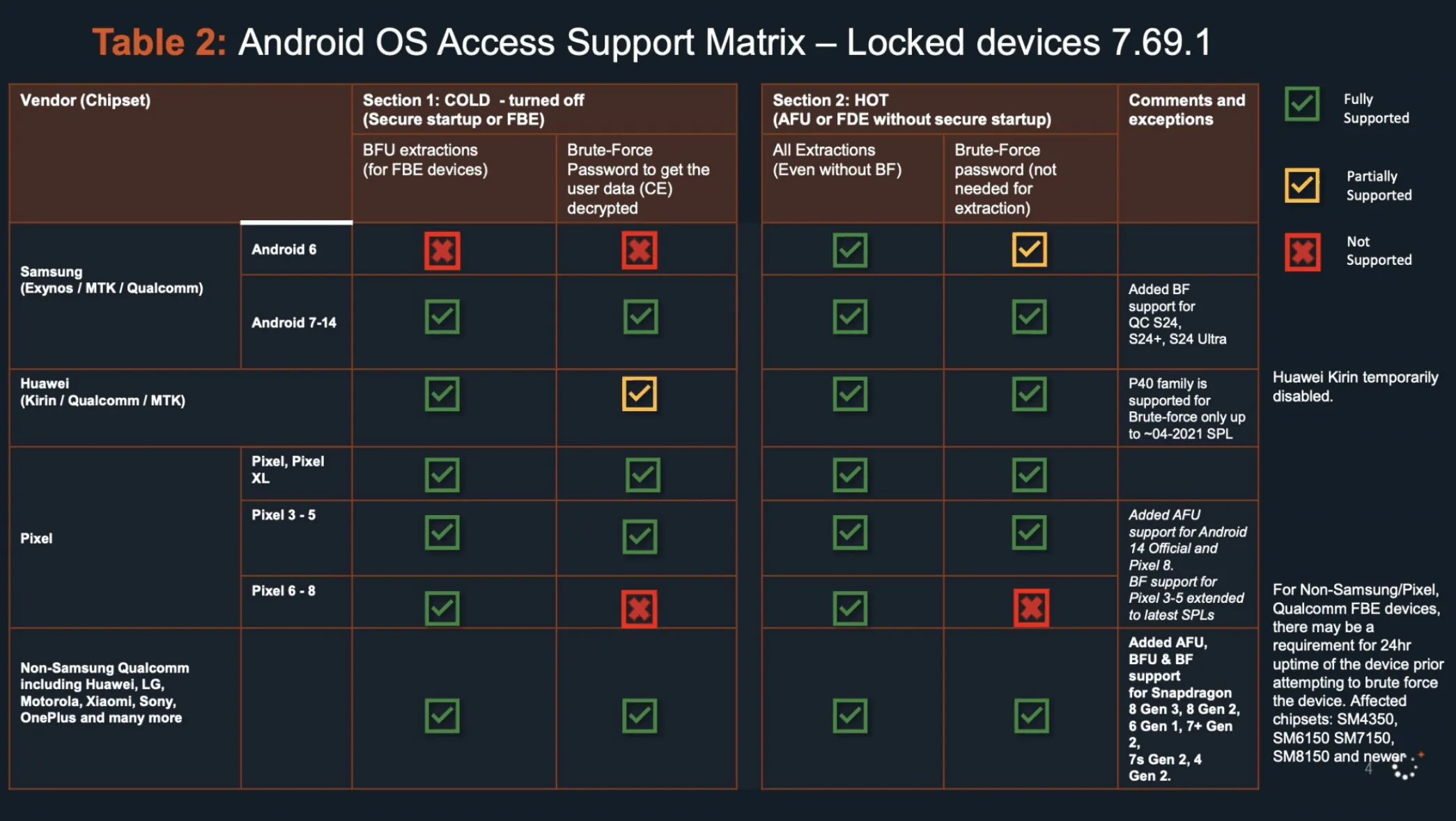
On the Android front, while Cellebrite has broader coverage for locked devices, they face challenges with Google’s Pixel series. The documents reveal that Cellebrite cannot brute force Google Pixel 6, 7, or 8 devices that have been powered off. The matrix also specifically mentioned GrapheneOS, a privacy-focused Android variant gaining popularity among security-conscious users.
While this sounds like good news for Pixel and iPhone users, Samsung users on the other hand might not be so lucky. The FBI managed to successfully accessed the phone of Thomas Matthew Crooks, the suspected shooter in an attempted assassination of former President Donald Trump.
The shooter reportedly had a Samsung phone that Cellebrite’s team managed to break into in just 40 minutes using their “secret” tool that’s still under development. It’s unclear if the company has managed to crack the code to finally get into Google Pixel or iPhone devices with the latest updates using this new tool.
According to these reports, investigators at the FBI’s Pittsburgh field office initially failed to open Crooks’ newer Samsung phone using existing Cellebrite tools. The device was then sent to the FBI lab in Quantico, Virginia, where agents contacted Cellebrite’s federal team. Cellebrite provided the FBI with an unreleased tool still in development, which successfully unlocked Crooks’ phone in just 40 minutes.
This case highlights the ongoing technological race between phone manufacturers and forensic tool developers. While Cellebrite’s current market tools struggle with newer operating systems, they are actively developing more advanced solutions.
Victor Ryan Cooper, Cellebrite’s senior director of communications, confirmed the authenticity of the leaked documents to 404 Media. He stated that these matrices are “designed to help our customers understand Cellebrite’s technology capabilities as they conduct ethical, legally sanctioned investigations.” Cooper also noted that Cellebrite does not openly advertise its capabilities to avoid aiding criminal activities.
Adding another layer to this digital forensics saga, someone on Reddit has allegedly leaked manuals for Cellebrite’s UFED (Universal Forensic Extraction Device) program. The leaked manuals reportedly contain detailed instructions, capabilities, and methods of how the device works. This information in the wrong hands could potentially be used by bad actors for nefarious purposes.
TechIssuesToday primarily focuses on publishing 'breaking' or 'exclusive' tech news. This means, we are usually the first news website on the whole Internet to highlight the topics we cover daily. So far, our stories have been picked up by many mainstream technology publications like The Verge, Macrumors, Forbes, etc. To know more, head here.