The tech world loves a good “Dieselgate” comparison, but rarely does it fit as perfectly as the latest allegations against Honey. If you drive a Volkswagen, you know the story: the car behaved one way when it knew it was being tested, and another way when it was out on the road. According to a deepening investigation by YouTuber MegaLag, the PayPal-owned shopping extension has been pulling a similar trick on millions of web browsers.
MegaLag released a video this week accusing Honey of running a “selective stand down” scheme. This comes as a major escalation after the YouTuber exposed the dark side of the Honey browser extension last year, alleging that the company’s practices have been questionable for some time. The core of the problem lies in how affiliate marketing works. When you click a link from a content creator, they are supposed to get credit for the sale.
Extensions like Honey are required to “stand down” so they don’t overwrite that creator’s cookie and steal the commission. But the investigation suggests Honey built a backdoor to bypass this rule, but only when it thinks nobody is watching.
The system reportedly profiles users to determine if they are “real” shoppers or compliance testers working for affiliate networks. If you look like a tester, using a fresh account, no history, no rewards points, Honey follows the rules perfectly. But if you look like a genuine consumer, the extension allegedly ignores the stand-down order and injects its own tracking, effectively poaching the revenue.
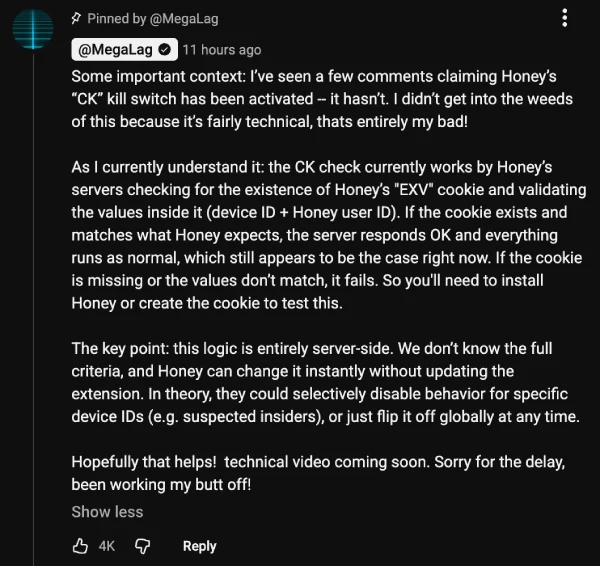
In a technical update posted after the video’s release, MegaLag clarified exactly how this digital switch works. It all comes down to a server-side check involving a cookie labeled “EXV.” This file contains your unique device ID and Honey user ID. Before the extension decides how to behave, it phones home.
If the server recognizes your device ID as a legitimate, profitable user, it sends the “OK” to run its aggressive scripts. If the cookie is missing or the values don’t match what the server expects (which is common during a compliance audit), the system fails over to a safe mode.
“The key point: this logic is entirely server-side,” MegaLag explained in a pinned comment. “They could selectively disable behavior for specific device IDs… or just flip it off globally at any time.”
This server-side control is what makes the behavior so difficult to pin down. You can’t just inspect the code in your browser to find the “fraud button” because the decision happens on PayPal’s computers, not yours. MegaLag noted that shortly after he began probing the system last year, PayPal quietly tweaked the parameters, raising the “safe” threshold to users with over 65,000 Gold points. This move likely limited the number of people affected to minimize risk while the company was under scrutiny.
Because the control switch is remote, Honey can theoretically toggle this behavior instantly without pushing a software update. For regular users, it means the extension in your toolbar might be checking your ID card before deciding which set of rules it wants to follow today.
TechIssuesToday primarily focuses on publishing 'breaking' or 'exclusive' tech news. This means, we are usually the first news website on the whole Internet to highlight the topics we cover daily. So far, our stories have been picked up by many mainstream technology publications like The Verge, Macrumors, Forbes, etc. To know more, head here.