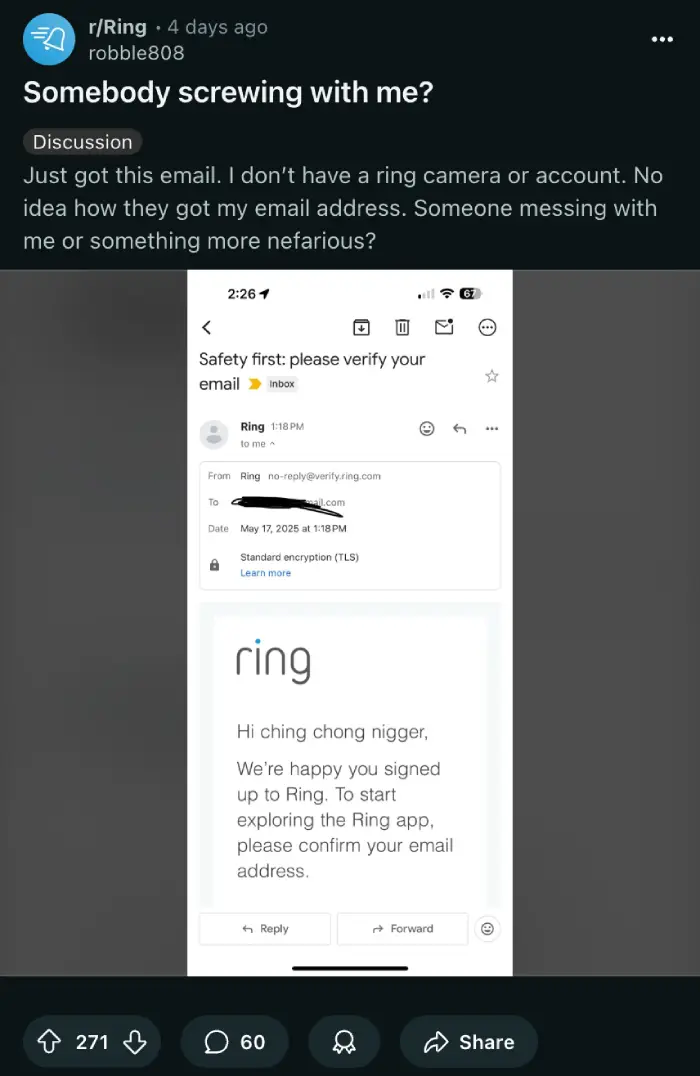
Imagine checking your inbox, only to find a new email from Ring, the popular video doorbell and home security provider that millions trust to protect their homes. But this isn’t your usual notification. The greeting is laced with vile, racist slurs, yet the email itself appears to be a legitimate account verification message. This unsettling scenario became a reality for numerous individuals over the weekend.
People began reporting these offensive emails, noting that they originated from official Ring email addresses, such as "[email protected]." This led many to initially fear a massive data breach or hack of Ring’s systems. One user on Reddit, with the username KFLLbased, confirmed their experience after examining the email in a controlled virtual environment, stating, “Yes, I opened the links on a virtual machine and it’s 100% legit from ring.” This user, like many others, had never even signed up for a Ring account or owned any of their products.
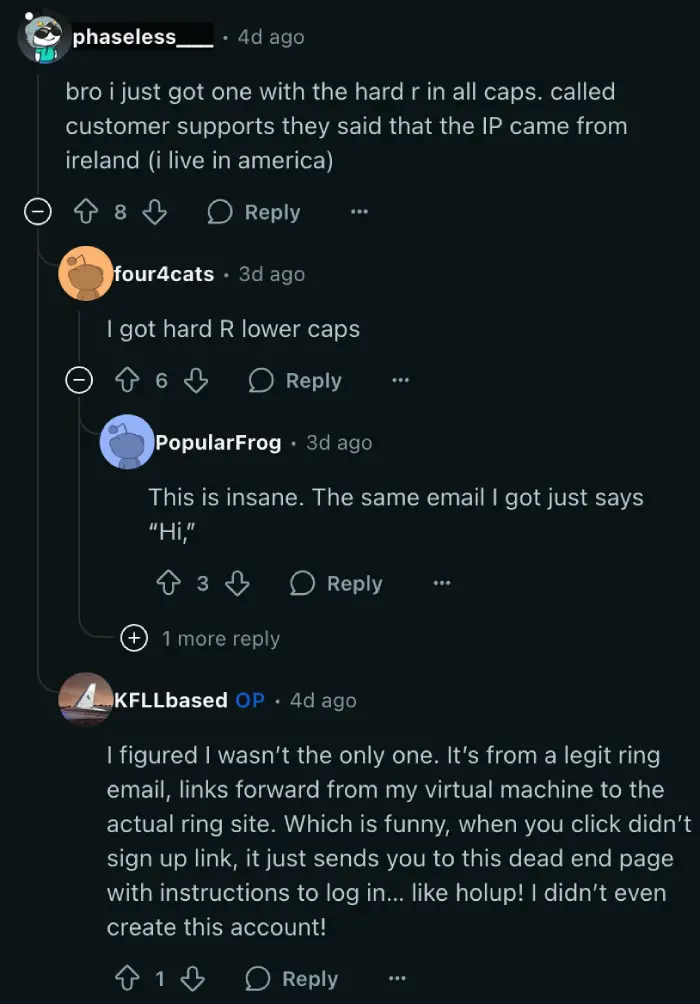
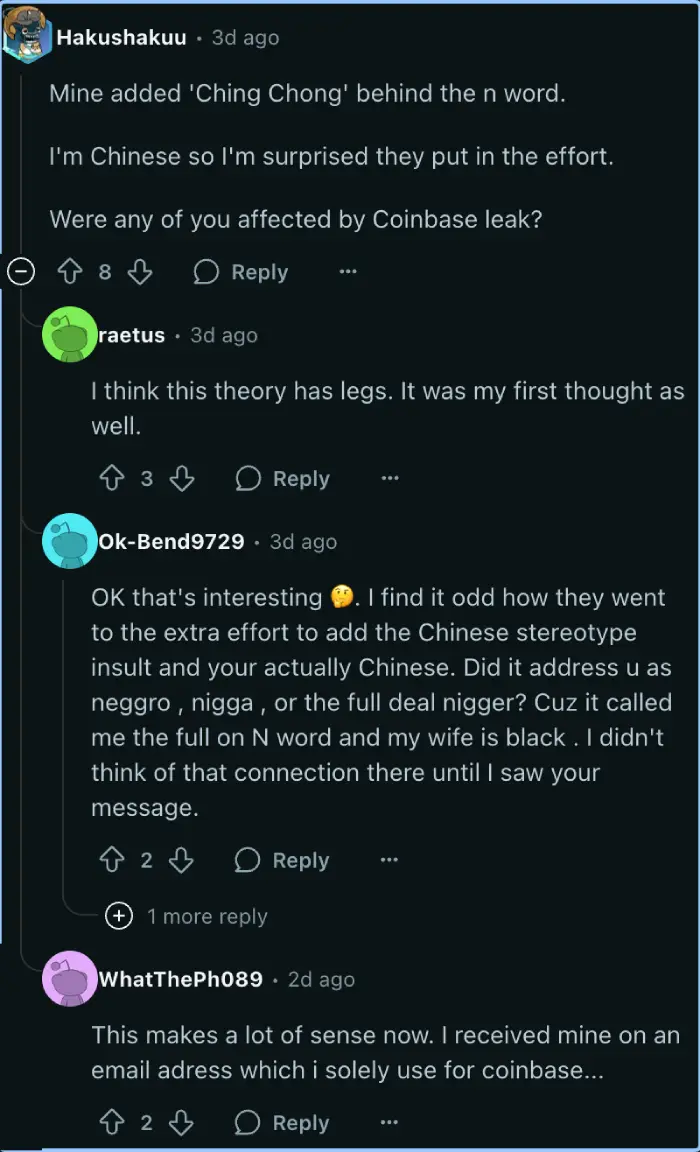
The nature of the racist content was particularly shocking. Users reported a variety of slurs. ClaydisCC, another Reddit user, shared, “Yeah mine said ching chong ni@@@. I just deleted, blocked, and didn’t click any links.” Others, like user phaseless___, recounted receiving messages with “the hard r in all caps,” and upon contacting customer support, were told the IP address responsible was traced to Ireland, despite the user being in America. User Hakushakuu noted a disturbing level of specificity: “Mine added ‘Ching Chong’ behind the n word. I’m Chinese so I’m surprised they put in the effort.”
It turns out, malicious actors hadn’t breached Ring’s core systems. Instead, they exploited the company’s publicly accessible account creation process. This system simply required a first name, last name, and an email address to trigger a verification email. Pranksters apparently obtained lists of email addresses, likely from unrelated data breaches circulating on the internet, and then automated the process of signing these emails up for new Ring accounts. For the “name” fields, they inserted the racist and offensive terms, which were then automatically included in the verification emails sent by Ring’s own servers.
Some users on Reddit began to theorize about the source of the emails used in the spam campaign. User WhatThePh089 commented, “This makes a lot of sense now. I received mine on an email adress which i solely use for coinbase…” suggesting a potential link to a previous data leak from the cryptocurrency platform.
Ring reportedly acknowledged the issue, stating, “We’re aware of an issue involving non-customers’ emails being used without their knowledge to create Ring accounts. These accounts appear to have been created by an unauthorized actor who obtained email addresses from a source other than Ring.” The company emphasized that this did not involve unauthorized access to existing customer accounts or information.
In response to the campaign, Ring began deactivating the maliciously created accounts. They also appear to have modified their verification email system. New account verification emails now reportedly use a generic greeting, such as “Hi, Neighbor,” instead of populating the name field with user-provided input, thereby closing off this particular avenue of abuse. User vertigo42 expressed frustration with Ring’s initial handling, mentioning, “How they don’t have a filter for names is beyond me. They also said I would have to be the one to remove my email from their system. Told them that was unacceptable.”
The incident, while not a direct hack of Ring, highlights how easily open systems can be manipulated for malicious purposes, spreading hateful content and causing distress to unsuspecting individuals. Matter of fact, not too long ago, we highlighted how scammers were targeting X users with almost legit looking emails. Before that, many people started getting emails from a legit @paypal.com email trying to trick them into calling the scammers.
So always double-check emails, and if you feel like it’s a scam, it most likely is. Never click on suspicious links or give out your password without being 100% sure that it’s the real deal. Stay safe out there!
TechIssuesToday primarily focuses on publishing 'breaking' or 'exclusive' tech news. This means, we are usually the first news website on the whole Internet to highlight the topics we cover daily. So far, our stories have been picked up by many mainstream technology publications like The Verge, Macrumors, Forbes, etc. To know more, head here.